
CSEE Department Distinguished Seminar
Accelerating Technology Disruption: The Cognitive Revolution
Dr. Arvind Krishna
Senior Vice President, Hybrid Cloud and Director, IBM Research
1:00-2:00pm, Friday, 24 February 2017, PAHB 132
Senior Vice President, Hybrid Cloud and Director, IBM Research
Digital disruption is changing the world around us, breaking down traditional barriers to market entry, creating new business models, and leading to new solutions to global challenges. Dr. Arvind Krishna will examine some of the core emerging technologies driving this phenomenon today, with an emphasis on artificial intelligence/cognitive computing. He will also share his perspectives on what it takes to build a successful, high-impact technical career in an era of disruptive innovation.
Arvind Krishna is senior vice president, Hybrid Cloud, and director of IBM Research. In this role, he leads the company’s hybrid cloud business, including strategy, product design, offering development, marketing, sales and service. He also helps guide IBM’s overall technical strategy in core and emerging technologies including cognitive computing, quantum computing, cloud platform services, data-driven solutions and blockchain. Previously, Arvind was general manager of IBM Systems and Technology Group’s development and manufacturing organization, responsible for developing and engineering everything from advanced semiconductor materials to leading-edge microprocessors, servers and storage systems.
Earlier in his career, he was general manager of IBM Information Management, which included database, information integration and big data software solutions. Prior to that, he was vice president of strategy for IBM Software. He has held several key technical roles in IBM Software and IBM Research, where he pioneered IBM’s security software business. Arvind has an undergraduate degree from the Indian Institute of Technology, Kanpur and a Ph.D. from the University of Illinois at Urbana-Champaign. He is the recipient of a distinguished alumni award from the University of Illinois, is the co-author of 15 patents, has been the editor of IEEE and ACM journals, and has published extensively in technical conferences and journals.




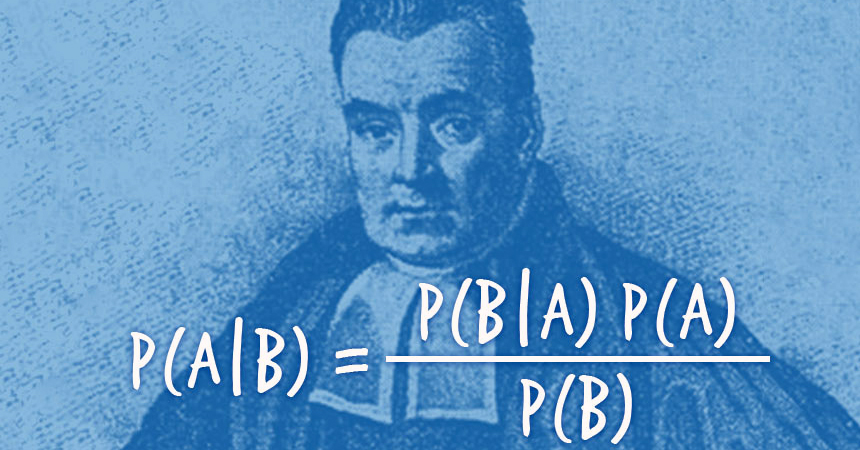

 Lexumo is a startup which provides the only automated service that continuously monitors IoT software platforms for the latest public vulnerabilities.
Lexumo is a startup which provides the only automated service that continuously monitors IoT software platforms for the latest public vulnerabilities. 





