M.S. Thesis Defense
Computer Science and Electrical Engineering
University of Maryland, Baltimore County
Fabrication and Characterization of a
Pd Nanowire-based Glucose Biofuel Cell
Kweku Amoah
10:30-12:30 Monday, 25 November 2013, ITE 346
Computer Science and Electrical Engineering
University of Maryland, Baltimore County
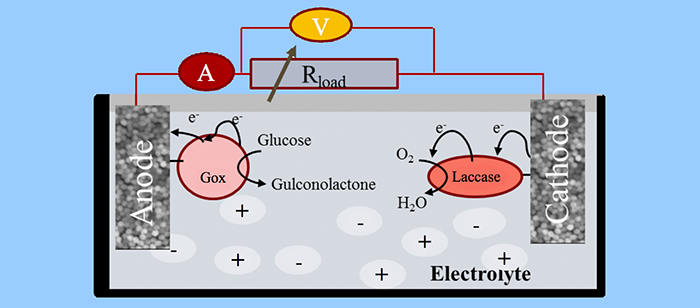
The use of glucose as a biofuel has received a lot of attention in part due to the potential applications of such systems. In addition to the being a clean energy alternative, it provides a pathway for implantable microelectronic devices such as pacemakers to be powered by interstitial fluid and eliminate the need for batteries. Furthermore, using interstitial fluid as power sources will drastically reduce necessary invasive surgeries to replace batteries. Additionally, cost to such patients will be reduced while quality of life enhanced. The research presents a unique platform for harvesting energy from glucose. Using semiconductor cleanroom techniques, electrically conductive palladium nanowires are grown on anodized aluminum oxide (AAO) templates using silicon and glass as supporting substrates. Photolithography is used to create two non-continuous gold windows and contact pads on the substrates. AAO templates are attached to the two gold windows and palladium nanowires are electrochemically grown on the AAO templates. Glucose oxidase and catalase are immobilized on the anode and laccase on the cathode. In the presence of glucose, electrons are released that generate voltage and current. The current-voltage behavior of the fuel cell, as well as electrochemical properties, is characterized using standard performance metrics. In 0.5 moles per liter of glucose solution with a neutral pH of 7.3, the open circuit voltage obtained was 335 mV and the short circuit current of 6 µA to yield a maximum power output of 2.01µW.
Committee: Drs. Gymama Slaughter (Chair), Fow-Sen Choa and Joel Morris