PhD Dissertation Proposal
Learning and Executing Energy Efficient, Context-Dependent
Rules for Privacy and Security Management on Mobile Devices
Prajit Kumar Das
8:00am Friday, 16 May 2014, ITE325b
There are ongoing security and privacy concerns around mobile platforms that are increasingly being used by citizens. For example a newly discovered security flaw in WhatsApp that allows hackers using a malicious app to read chat messages stored on the SD card. The Brightest Flashlight application was reported to have logged precise location and a unique user identifier, which have nothing to with its intended functionality. Current mobile platform privacy and security mechanisms are limited to an initial installation phase permission acquisition method. In addition to that, the permissions are of the all or none form. This means that either the users accept all the permissions requested by the mobile app or they cannot use the app in question. Even if permissions were not structured as such, typically, users do not understand the permissions being requested or are too eager to use the application to even care to read them. These issues are present in all major mobile operating systems. Given the penetration of mobile devices into our lives, a fine-grained context-dependent security and privacy control approach needs to be created.
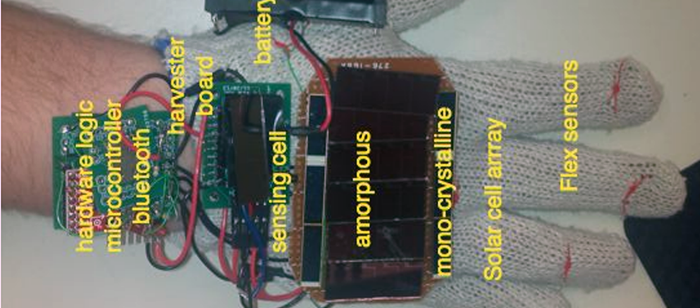
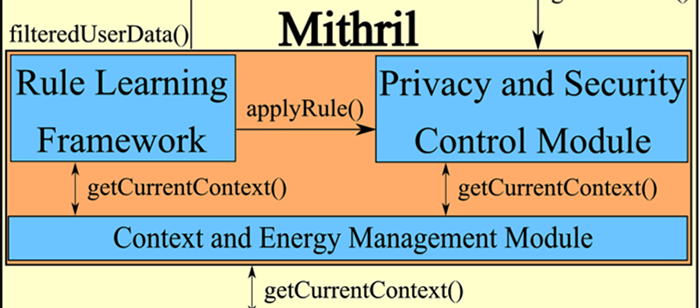
We propose a framework that will allow us to learn the privacy and security rules for a particular user, on their mobile devices. We do this by employing a simple user feedback mechanism. The rule learning framework consists of a “learning mode” where it observes and learns from user behavior and a “working mode” where it implements the learned rules to protect user privacy and provide security. The rules are represented to the user in plain English using an easily understandable construct. The rules are internally written in a logic based language and using Semantic Web technologies. The antecedents of the rules are context elements that are derived from an ontology using a query engine and an inference mechanism. The main contributions of our work include learning modifications to current rules and learning new rules to control the data flow between the various data providers on the user’s mobile device, including sensors and services and the consumer of such data. The privacy and security rule execution consumes significant energy due to the context detection. We create an energy model that allows us to make energy cost optimizations with regards to rule execution. We use a three-fold solution for achieving the said energy cost optimizations.
Committee: Drs. Anupam Joshi (chair), Nilanjan Banerjee, Dipanjan Chakraborty (IBM), Tim Finin, Tim Oates, Arkady Zaslavsky (CSIRO)