MS Thesis Defense
Comparison of Cloud Security Standards and a
Cloud Security Control Recommendation System
Amit S. Hendre
8:30am Thursday, 31 July 2014, ITE346
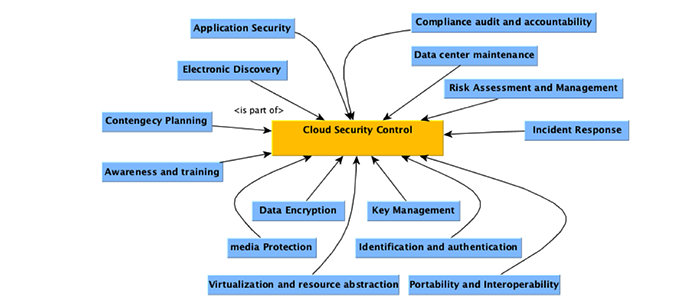
Cloud services are becoming an essential part of many organizations. Cloud providers have to adhere to security and privacy policies to ensure their users’ data remains confidential and secure. On one hand, cloud providers are implementing their own security and privacy controls. On the other hand, standards bodies like Cloud Security Alliance (CSA), International Organization for Standards (ISO), National Institute for Standards and Technology (NIST), etc. are developing broad standards for cloud security. In this thesis we provide a comprehensive analysis of the cloud security standards that are being developed and how they compare with the security controls of cloud providers. Our study is mainly focused on policies about mobility of resources, identity and access management, data protection, incident response and audit and assessment. This thesis will help consumer organizations with their compliance needs by evaluating the security controls and policies of cloud providers and assisting them in identifying their enterprise cloud security policies.
Committee: Drs. Karuna Joshi, Tim Finin and Yelena Yesha







