 Professor Anupam Joshi, chair of the CSEE Department and director of the UMBC Center for Cybersecurity
Professor Anupam Joshi, chair of the CSEE Department and director of the UMBC Center for Cybersecurity
With a new administration in the White House, securing the president’s smartphone is a national security priority, but exactly what steps are taken to secure the phone are not made public. In a new article in The Conversation, Anupam Joshi, professor and chair of computer science and electrical engineering, and director of the Center for Cybersecurity at UMBC, discusses several likely ways President Trump’s security team is building protections into his phone, through everything from hardware to settings to app restrictions.
Limiting the number of people who have the president’s new phone number and keeping the unique International Mobile Equipment Identity number guarded can prevent potential attackers from accessing confidential information stored on the phone. This method is called “security by obscurity,” says Joshi.
Joshi also says the device Trump will use was likely made by a trusted manufacturer with carefully created and checked parts, explaining that this minimizes the “risk that the hardware would have any vulnerabilities that an attacker could exploit.”
Customizing the operating system, and allowing the phone to connect only with predetermined networks that are regularly monitored can also help protect against attacks, says Joshi. “Limiting its contact with the internet would, of course, by key,” he notes, “though that would also significantly limit the phone’s usefulness to a president whose routine involves constant connection.” Joshi says that limiting the number of apps on the phone, reducing the ability for additional apps to be downloaded and installed, and disabling automatic updates to the phone could keep the device even more secure.
While it is not certain which methods have been employed to secure the presidential smartphone, Joshi says that Trump trading in his commercial-grade phone for a government-secured device is an important first step in protecting the U.S. from hacks and attacks.
In another article in The Conversation, Rick Forno, assistant director of the UMBC Center for Cybersecurity and director of the Cybersecurity Graduate Program at UMBC, addresses the importance of addressing both short-term and long-term cybersecurity issues. He explains that ignoring underlying problems and only addressing small, attention-grabbing issues does not lead to lasting progress. “Cyber-fatigue,” explains Forno, is an “inability to think critically about what needs to happen for meaningful, lasting cybersecurity improvements while focusing only on near-term problems.”
He says that while it is important to evaluate the benefits, conveniences and savings that new products and services may offer, the potential risks and problems should be considered, too. “So instead of repeating the same guidelines and recommendations of the past, it’s time to take a new and unconventional look at our approach to technology and how we secure it,” Forno explains. “Unless we’re willing to go beyond our traditional cybersecurity ‘comfort zone’ and explore new solutions, our cyber-fatigue will worsen.”
Read “How to secure a smartphone for the tweeter-in-chief” and “Overcoming ‘cyber-fatigue’ requires users to step up for security” in The Conversation. Joshi’s piece also appeared in Mashable and Channel Newsasia, and together the articles have already been read over 36,000 times.
Adapted from UMBC News, photo by Marlayna Demond ’11 for UMBC.






 Alejandra Diaz, left, with fellow Cyber Scholars. Photo by Marlayna Demond ’11 for UMBC.
Alejandra Diaz, left, with fellow Cyber Scholars. Photo by Marlayna Demond ’11 for UMBC. Professor Anupam Joshi, chair of the CSEE Department and director of the UMBC Center for Cybersecurity
Professor Anupam Joshi, chair of the CSEE Department and director of the UMBC Center for Cybersecurity
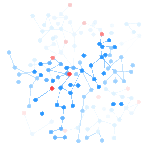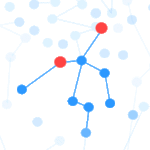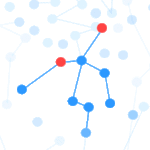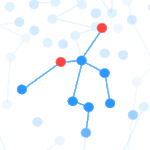 Lexumo is a startup which provides the only automated service that continuously monitors IoT software platforms for the latest public vulnerabilities.
Lexumo is a startup which provides the only automated service that continuously monitors IoT software platforms for the latest public vulnerabilities. 

 “I am most excited about the opportunity to work for a member of Congress and to learn how the legislative process flows. It will be a huge time for change on Capitol Hill—a new president and many newly elected officials. I would like to bring my technical knowledge to the Hill as those new officials discuss legislation relating to cybersecurity,” she said.
“I am most excited about the opportunity to work for a member of Congress and to learn how the legislative process flows. It will be a huge time for change on Capitol Hill—a new president and many newly elected officials. I would like to bring my technical knowledge to the Hill as those new officials discuss legislation relating to cybersecurity,” she said.