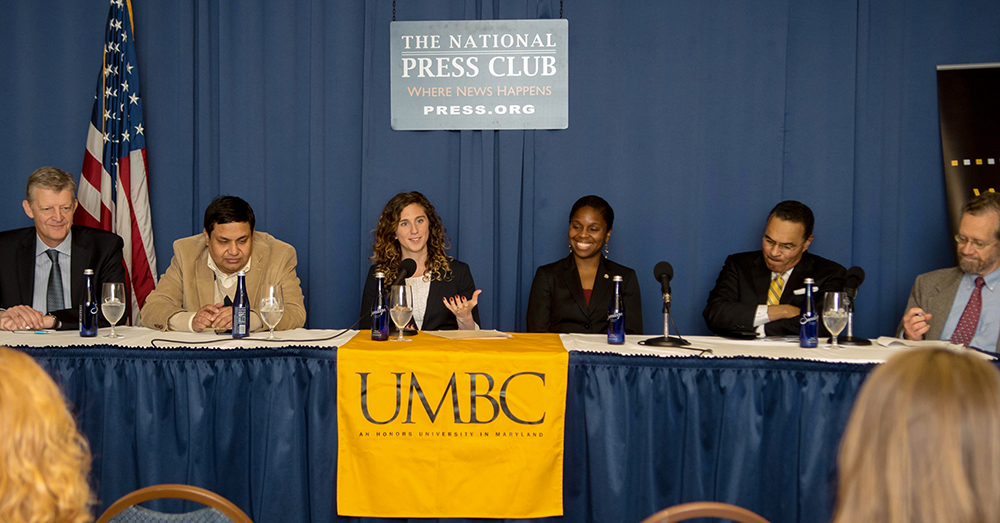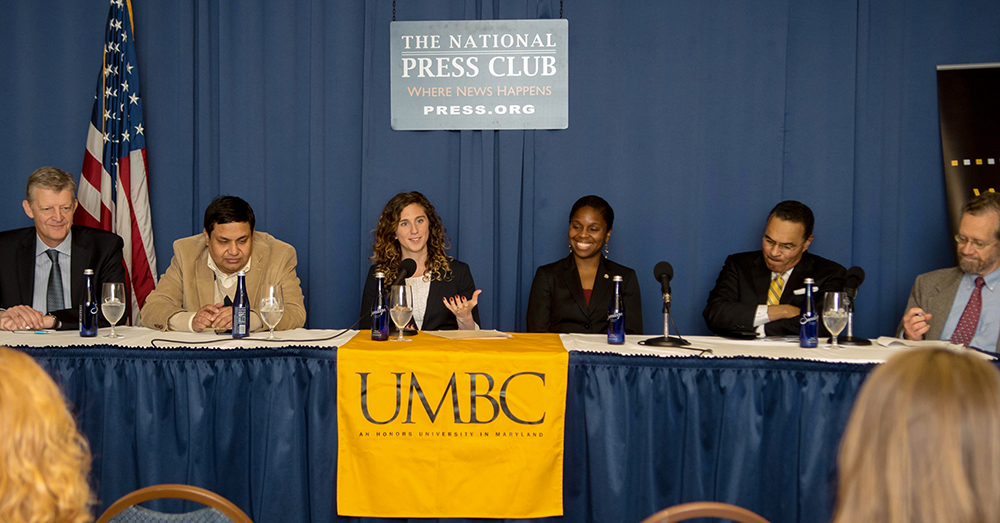
UMBC faculty, alumni and corporate partners discuss cybersecurity and industry challenges
Cybersecurity is regularly a headliner in the news, especially when personal information stored online has been compromised, whether through a breach, hack, or threat. On Thursday, December 7, UMBC hosted experts from industry and academia at the National Press Club to discuss the cyber challenges professionals face, and how those groups can work together to prepare future generations of cybersecurity professionals.
Scott Shane, a reporter with The New York Times, led the discussion with five panelists representing industry, small business, and higher education. “I think it’s fair to say the internet was built without adequate attention to security,” stated Shane, who writes about cyber and information attacks regularly. “It’s almost like somebody who starts a bank with branches all over the world, and after it’s up and running and has millions of account holders, suddenly starts to think about safes, locks on the doors and bulletproof glass. I think that’s sort of the stage that we’re at right now.”
UMBC President Freeman Hrabowski and Anupam Joshi, professor and chair of computer science and electrical engineering, and director of the Center for Cybersecurity at UMBC, were joined by alumni and partners who have been working on the challenge of educating the workforce together. Hrabowski explained that there are currently about 350,000 unfilled cybersecurity jobs, and that number is expected to continue to grow. By 2021, it is anticipated that there will be approximately three million job openings in cyber-related fields.
Over the course of his professional career, Nigel Faulkner, chief technology officer at T. Rowe Price, has experienced the emergence of technology and many changes. “As the CTO of a medium-large company, cyber is a defensive investment for us. The best thing that can happen is nothing happens,” Faulkner said, adding that he is always thinking about whether the company is investing enough, doing the right thing, and making the right connections in the industry to keep clients’ information safe.
As president and founder of TCecure, LLC, and cybersecurity academic innovation officer for University System of Maryland (USM), Tina Williams ’02, computer science, shared the importance of building security into technology from the beginning, rather than adding these features on at the “tail end of a development cycle.” Not only does her company handle security, they also monitor threats and risks that can compromise the technology’s health. In her role at USM, Williams represents the system as a whole to integrate academia and academic research, relationships, and resources into what’s taking place nationally, at the Federally Funded Research and Development Centers.
As head of UMBC’s Center for Cybersecurity, Joshi explained that UMBC is combating these national challenges by partnering with industry and government leaders to conduct research that addresses specific real-world needs that benefit both. Collaborative relationships, such as UMBC’s work with Northrop Grumman and T. Rowe Price, is one way that UMBC is working to cultivate the next generation of cybersecurity talent.
As an alumna of UMBC and a current employee at Northrop Grumman, Lauren Mazzoli ’15, computer science and mathematics, M.S. ’17, computer science, a systems engineer in the Future Technical Leaders Program at Northrop Grumman, discussed her experience in the Cyber Scholars Program. The Cyber Scholars Program works to increase the participation of women and underrepresented minorities in the field. Mazzoli explained that her experience at UMBC, in the Cyber Scholars Program, and working alongside mentors on and off-campus led her to be involved with continuing to encourage women to pursue careers in cybersecurity. “For me it’s been a product of the relationship between academia and industry, that have allowed me to find my own career path, and at the same time help others find theirs,” she explained, noting her passion for helping students consider careers in cybersecurity and related fields.
“We know there’s a huge workforce that we need and we can’t fill that pipeline. So yes, we need more women, yes, we need students of all backgrounds, but we need diversity of thought, experience, education, and problem-solving skills,” said Mazzoli, adding that it is important for students to know from a young age that cybersecurity is a field they can pursue.
Adapted from a UMBC News article article written by Megan Hanks Photo by Abnet Shiferaw ’11, visual arts.